Log Management On-Premises
How much time do you waste managing log files?
How much does it cost to fail to detect possible unwanted access to IT infrastructure and company data?
If you need to adapt your computer network to current regulations (e.g. GDPR) and security compliance (e.g. P.C.I., 27001), COALA is the right solution!
COALA is the complete software available in on-premises mode for log management and analysis that meets the corporate compliance, security and control needs of any type of company, private or public.
Key Features
It acquires, centralizes and archives logs
ensuring their completeness, inalterability and integrity for compliance purpose
It constantly monitors the security
of all data processing processes, responding to the needs of the EU Regulation 2016/679 (GDPR) by System Administrators (AdS)
It offers different types of analysis
useful both for regulatory compliance and for monitoring and verifying system usage and information security
It allows you to set real-time alarms
based on log content and monitoring dashboards to promptly identify system anomalies and data access issues
It produces basic, detailed and customized reports
come strumenti a supporto di verifiche pianificate e come documentazione dei risultati dei controlli periodici
It builds a reliable and comprehensive database
fundamental for the correctness of any type of analysis, debugging activity and anomaly detection
It reduces time, personnel and infrastructure resources
dedicated to compliance management
What it allows you to do
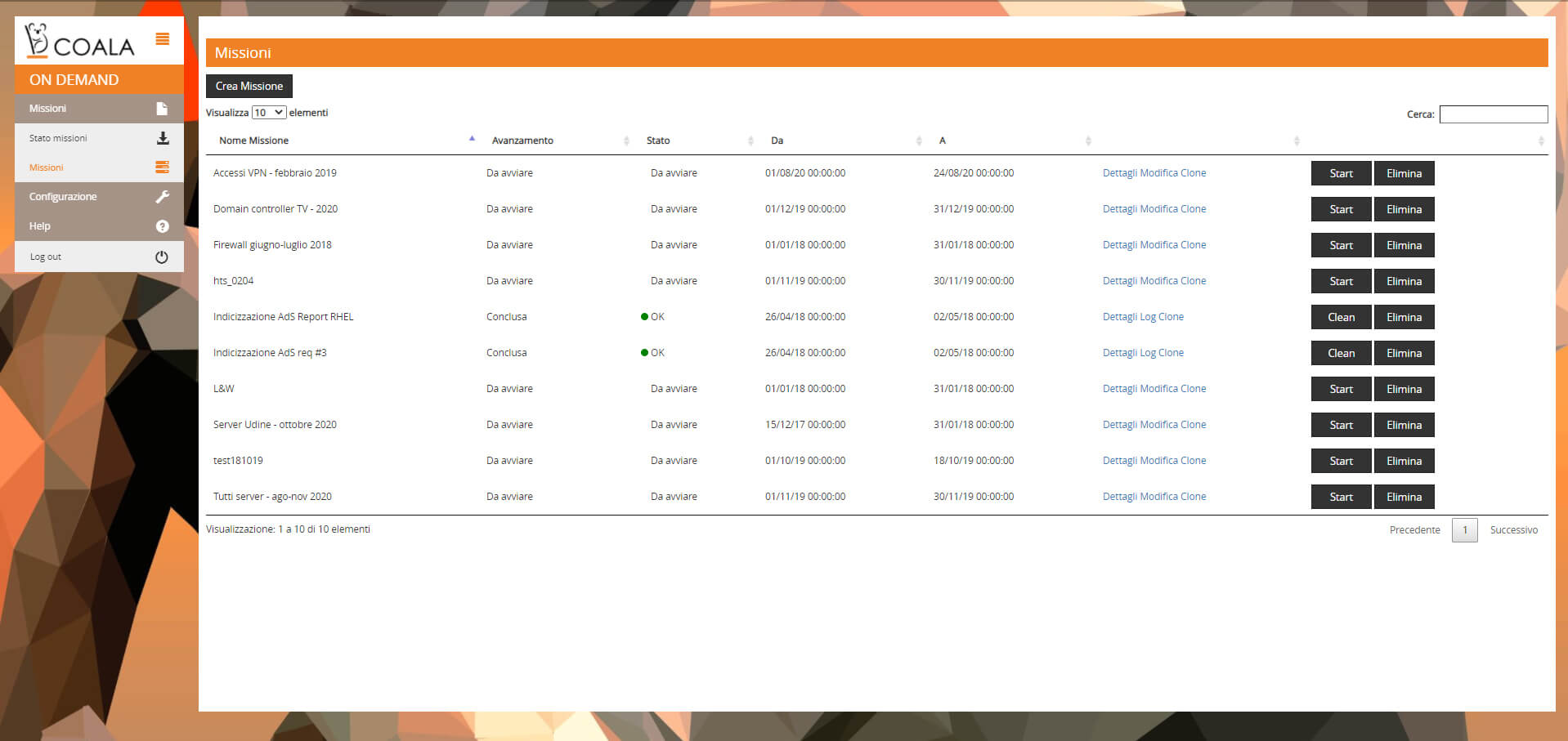
Coala is available in on-premises mode and consists of 5 modules, each with its own functionality:
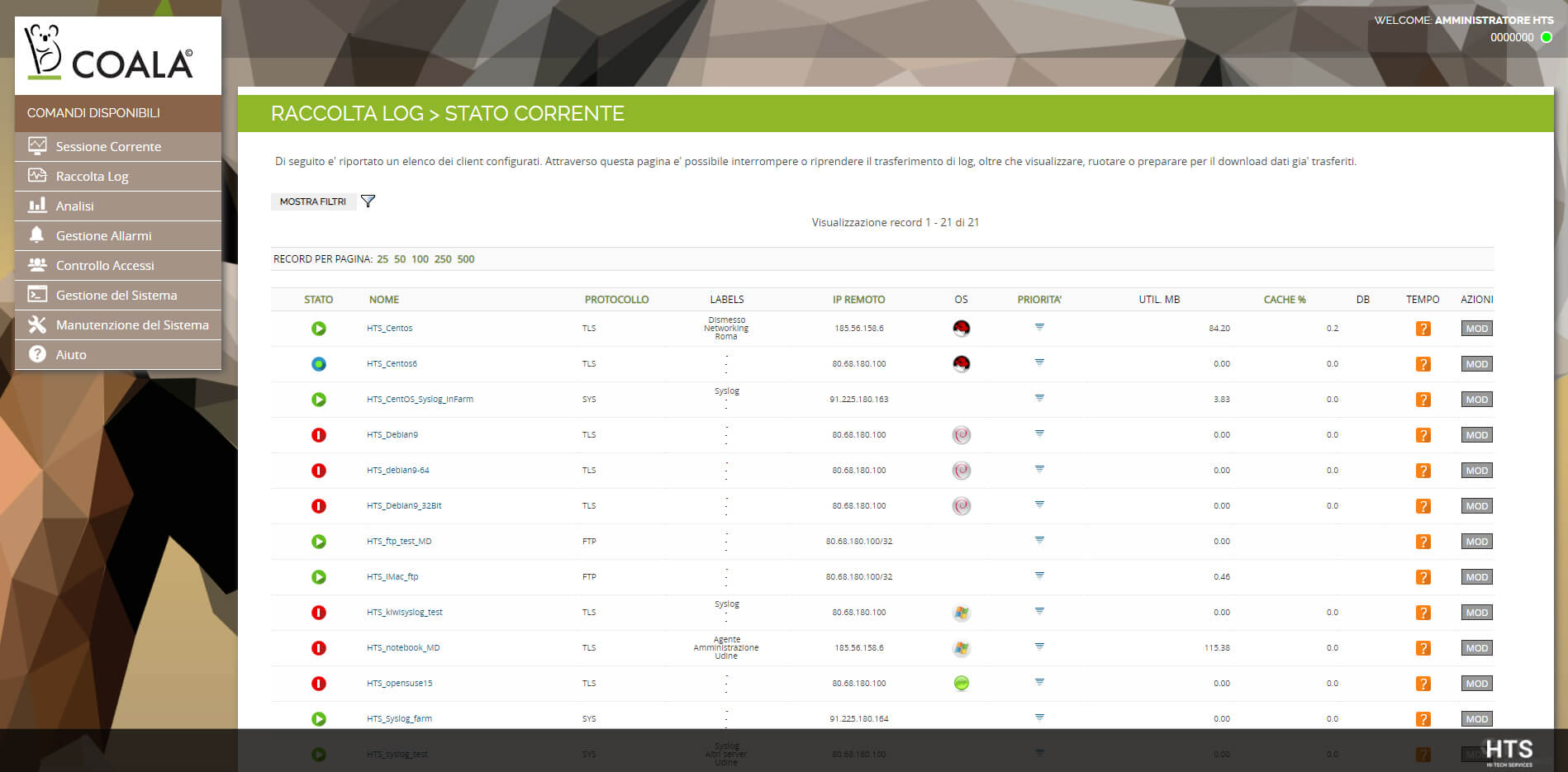
Collector
- Real-time acquisition with agent or agentless
- Centralized configuration and monitoring
- Raw format logs and data security (transport, storage, etc.)
- Automatic log deletion based on configurable retention and differentiable by log source
- System alerts for malfunction anomalies
- Internal logs of operations and operating status
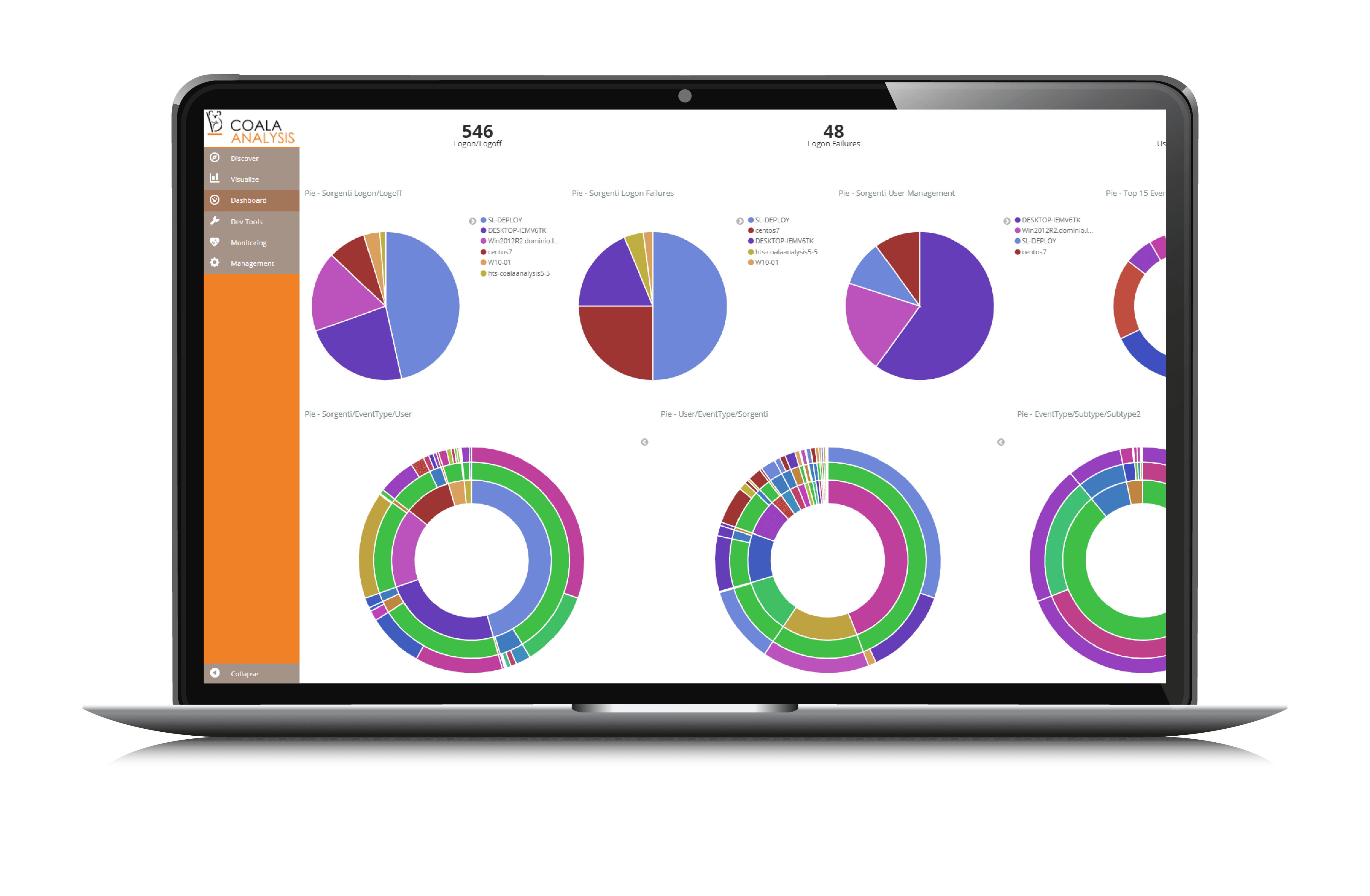
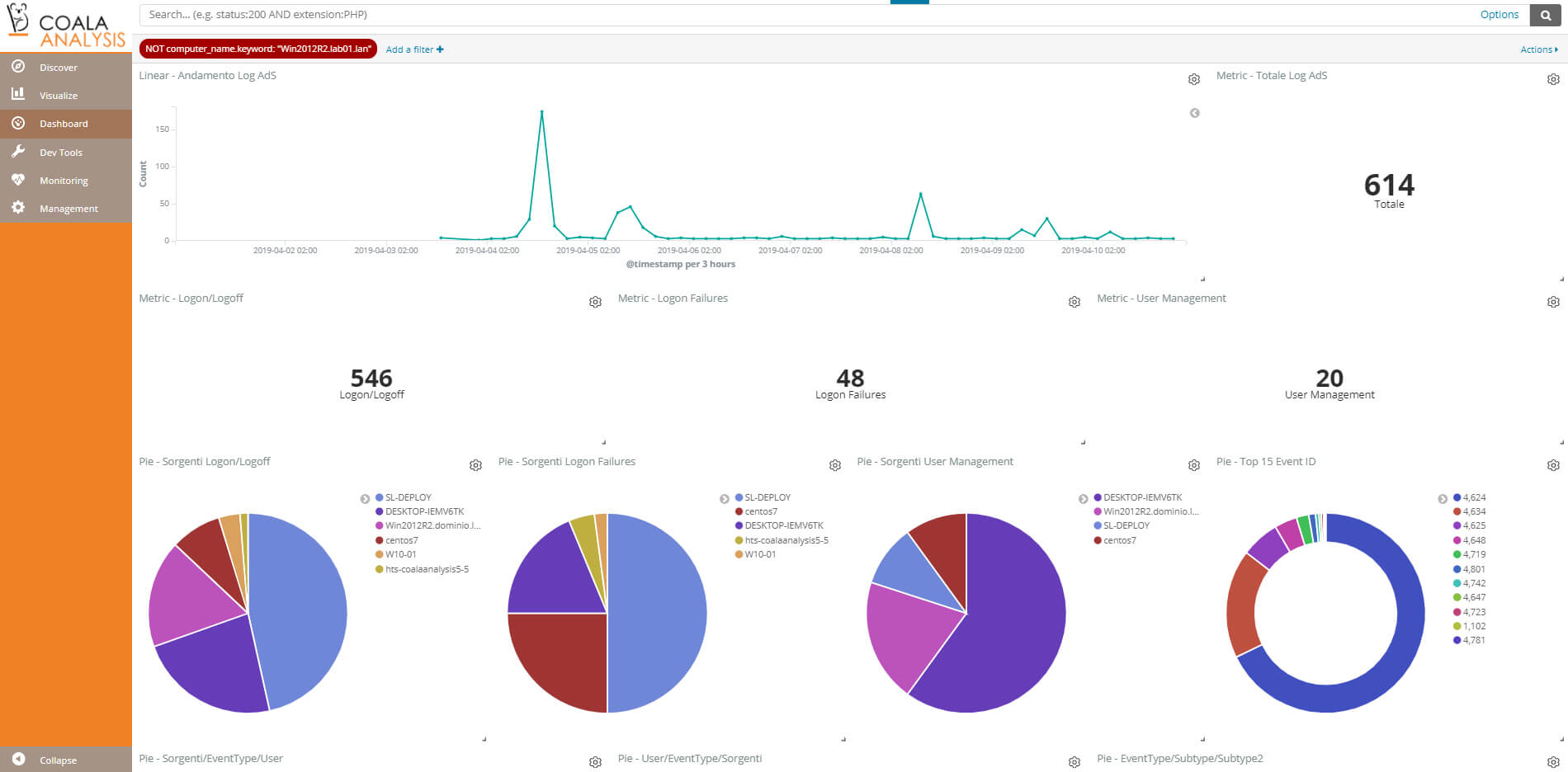
Analysis Real Time
- Real-time analysis and indexing
- Full-text search
- Monitoring dashboard
- Custom analysis templates
- Integration with other modules for advanced analysis
Analysis On Demand
- Indexing and analysis of data based on needs (e.g. requests for retrospective verifications)
- Complementary analysis (e.g. time interval) or independent of real time
- Integration with real-time for optimization of infrastructure resources (e.g. storage)
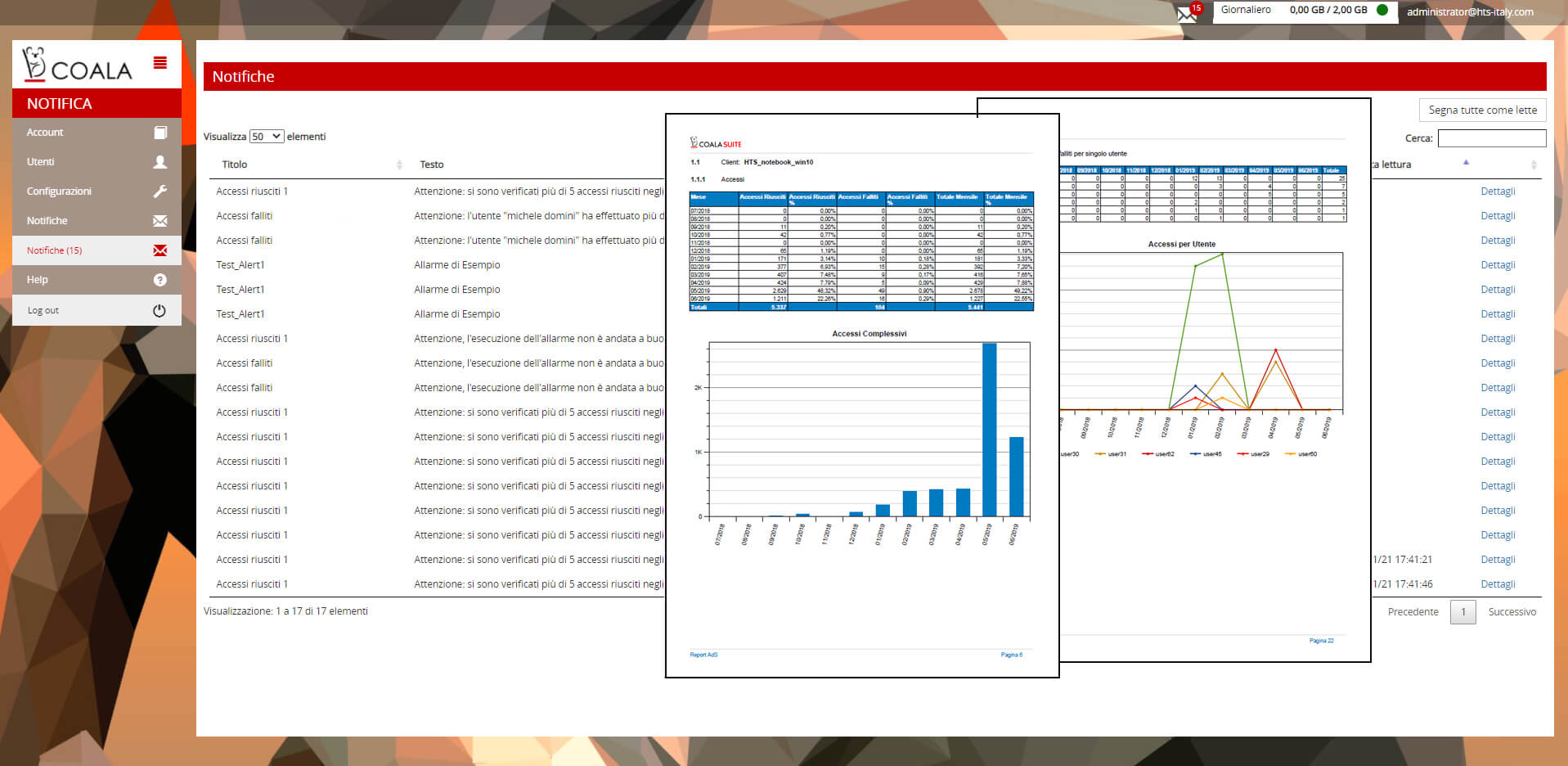
Report
- Self-managed report management
- On-demand, periodic and scheduled reports
- Included standard report templates
- Custom report templates
- Historical archive of produced reports
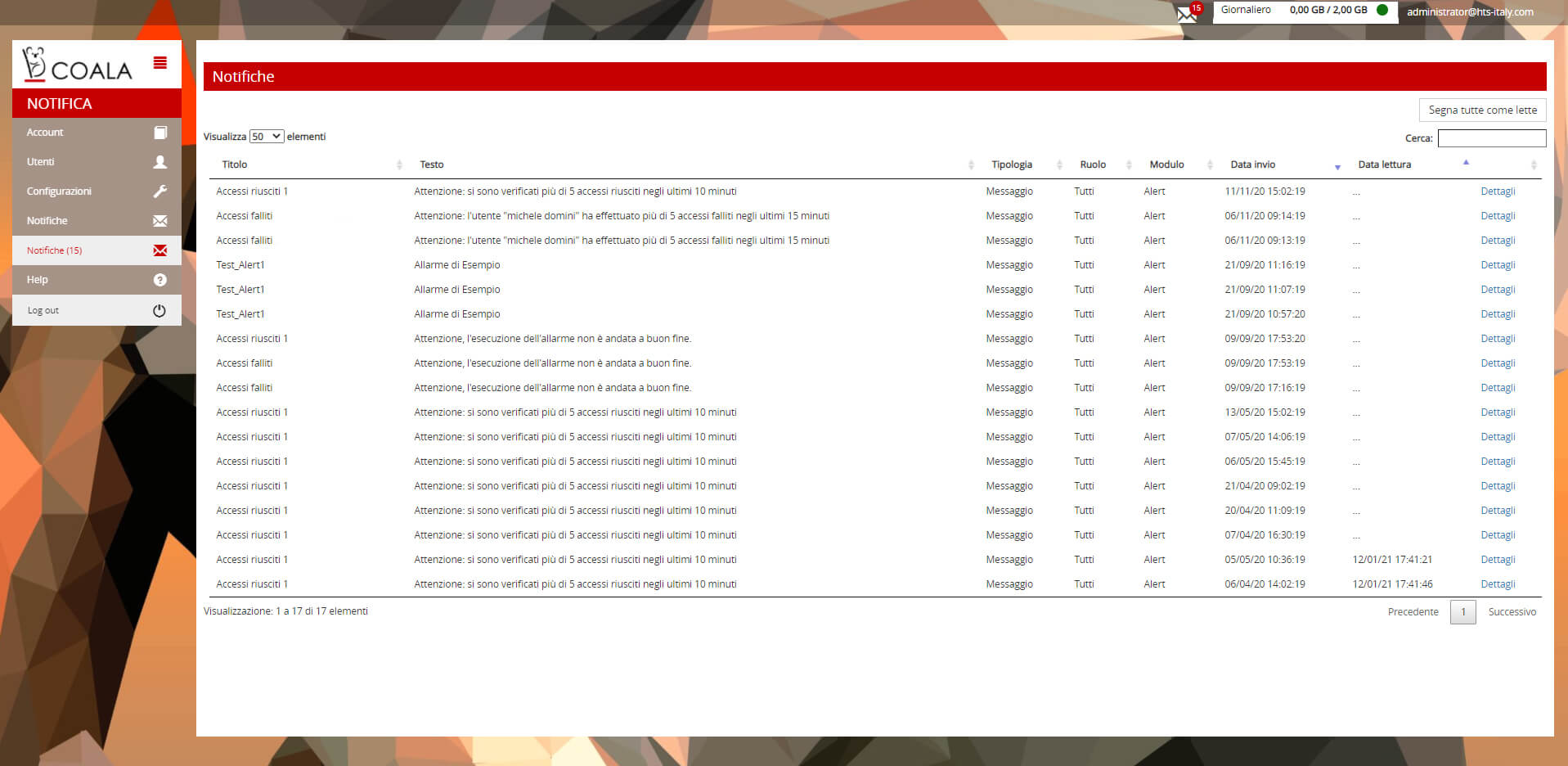
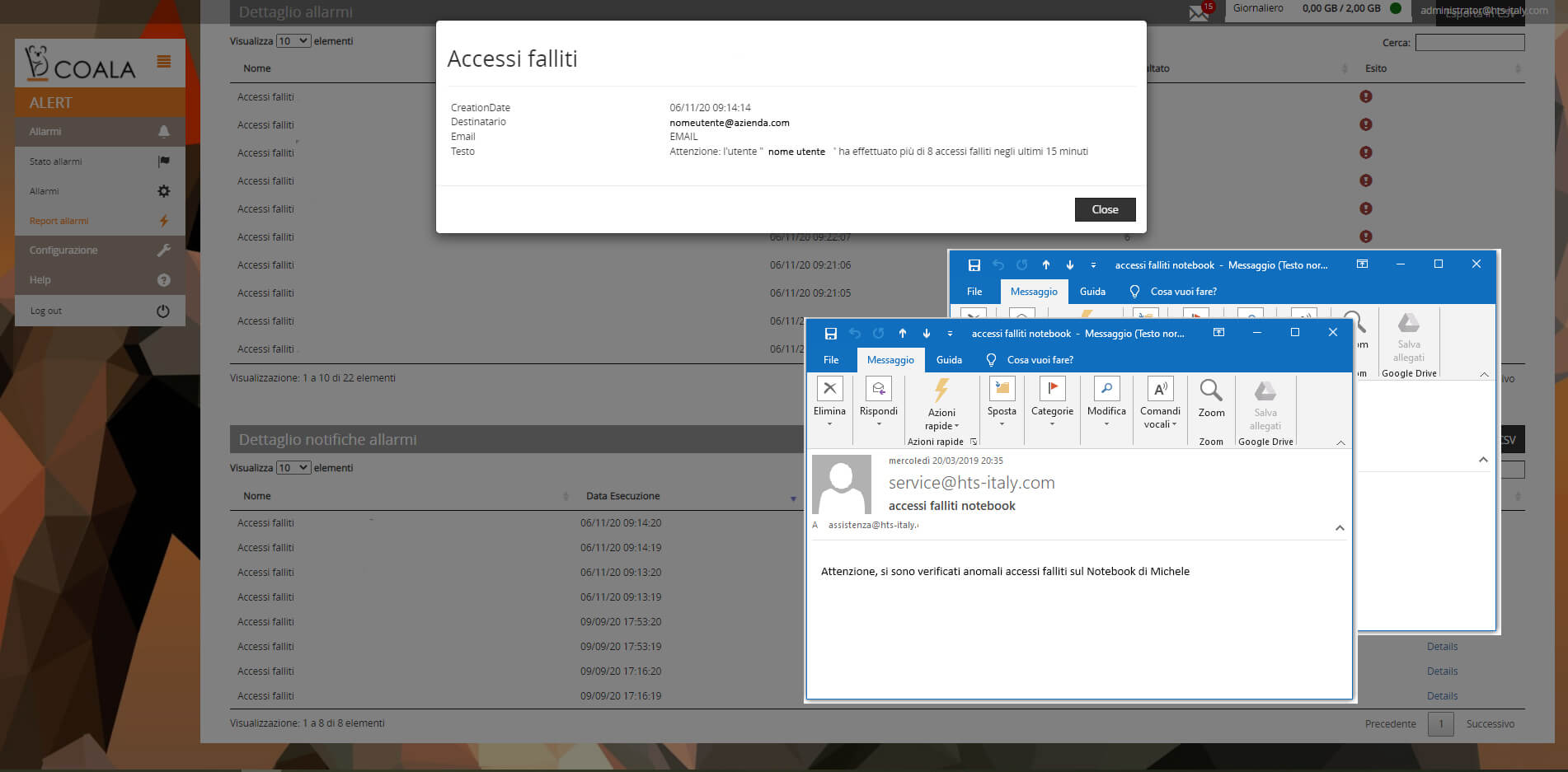
Alert
- Configurable alarms based on log content
- “Manual” and catalog alarms
- Included standard alarm catalog
- Custom alarm catalog
- Centralized consultation and verification of the history of alarms and notifications generated (email, snmp, etc.)
Do you want a Log Management solution in the cloud?
Discover LOGBOX ➔Together with Coala
HTS consultancy and services
Log management for compliance and security purposes requires experience and knowledge of best practices and regulatory standards.
In addition to the COALA solution, HTS provides its customers with consulting and training services: through its team of certified professionals, HTS is able to support digital transformation projects from the analysis of the existing situation to the deployment of the necessary tools for monitoring and Log Management

➔ Contact us for more information